This page will help you identify and fix issues. If you encounter any issues while performing test configuration and SAML SSO then you can follow below knowledgeBase to fix it very quickly.
Test Configuration Failed
SAML SSO Failed
1. Test Configuration Failed
If the test configuration has been performed in the plugin's IDP configuration tab and results Test Failed, the possible causes are listed below.
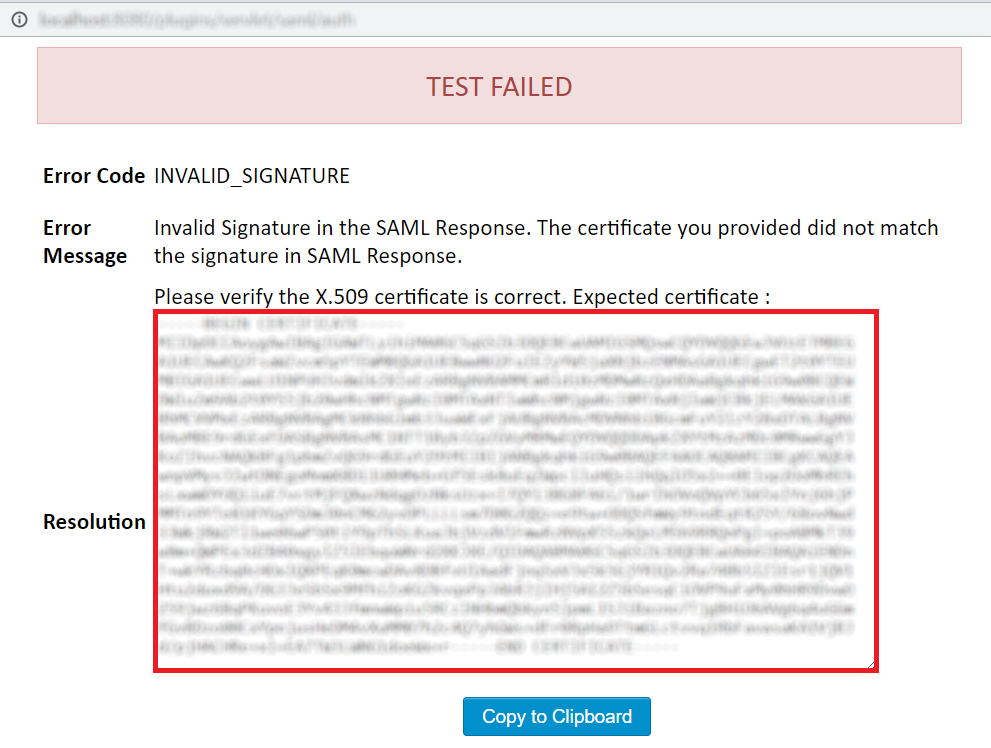
Error Code: INVALID_SIGNATURE
Description: This issue comes when the configured certificate in the plugin's configure IDP tab did not match the Certificate in SAML Response.
How can it be fixed?:
Copy Expected Certificate from Test window.
Paste it in the IDP Signing Certificate text box in Configure IDP Tab.
Save settings.
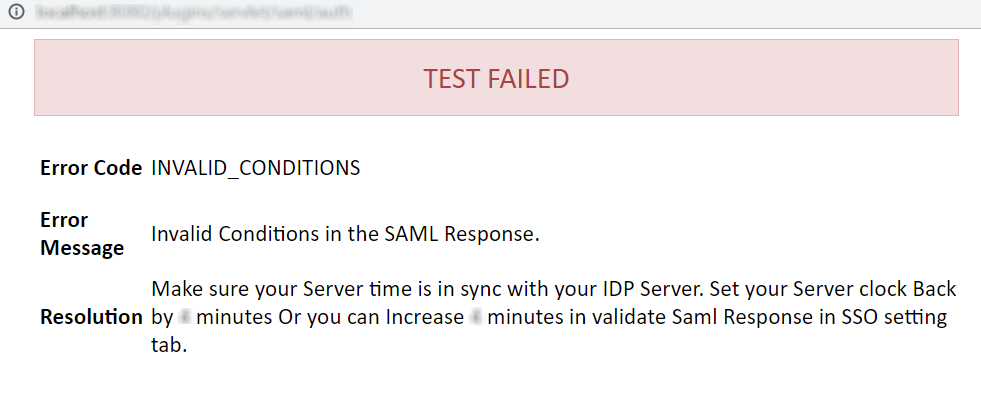
Error Code: INVALID_CONDITIONS
Description: This issue generally comes up when the Application(Jira, Confluence, Bitbucket, Bamboo, and fisheye) server's time is not within the time interval specified by IDP in SAML Response. Hence, the SAML Response gets invalidated and the SAML app is unable to proceed it even if the difference is in milliseconds.
How can it be fixed?:
Read Resolution in the Test window and note the value of the minutes which you need to set in Validate SAML Response.
Go to the SSO settings tab in the plugin scroll down to Advanced SSO settings and change the value of Validate IDP's SAML Response to minutes mentioned in the Test window and save it.
Go to Configure IDP tab in the plugin try Test configuration again.
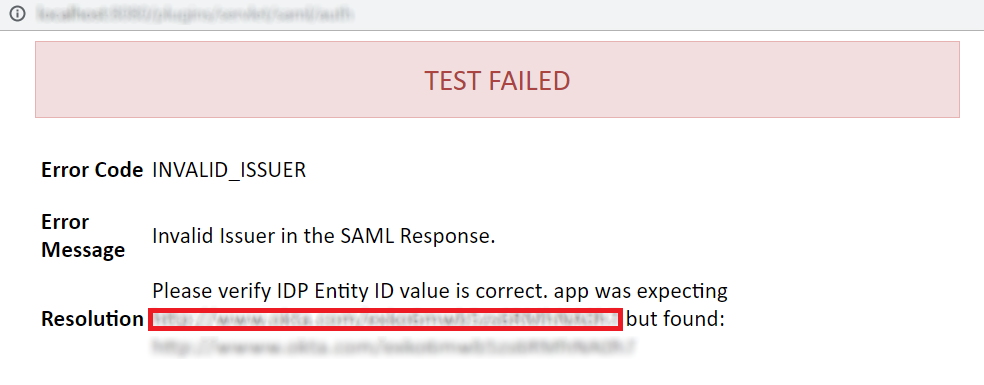
Error Code: INVALID_ISSUER
Description: This problem will come when the IDP entity ID / Issuer configured in the plugin does not match with the IDP Issuer.
How can it be fixed?:
Copy the value of the Issuer from the Test window. For the reference shown in the picture below.
Paste it in the IDP Entity/Issuer text field in the configure IDP tab of the plugin.
Save settings.
2. SAML SSO Failed
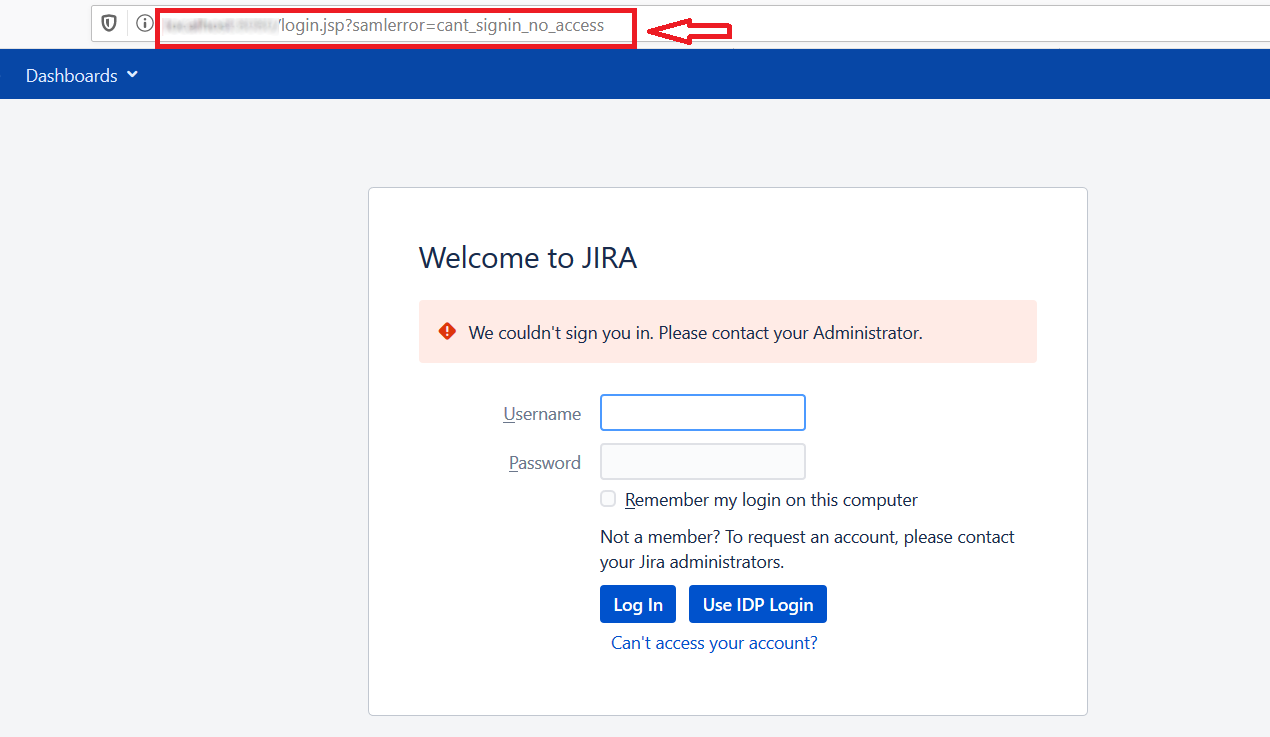
If the Test Configuration Results Success and SAML SSO Failed, the possible causes are listed below. Please check the URL and find the below-mentioned parameter in the URL.
Error Code: samlerror=cant_signin_no_access
Description: This problem will come when the user tries to login in Atlassian application and the user has no permission to log in.
How can it be fixed?:
Add the user to an application group that gives login permission.
Follow this knowledgeBase to assign a group to the user which gives access to the application.
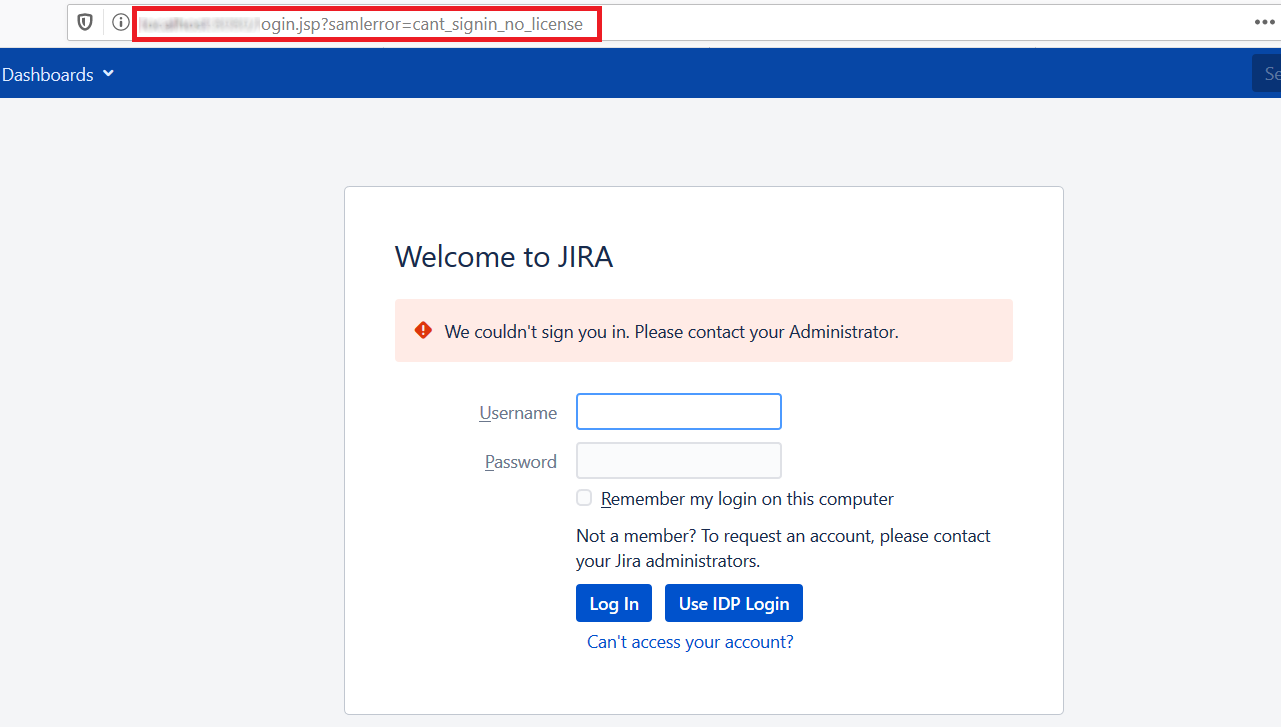
Error Code: samlerror=cant_signin_no_license
Description: No license exits. Single Sign-On will not work unless an app license is applied.
How can it be fixed?:
Update license in manage apps sections.
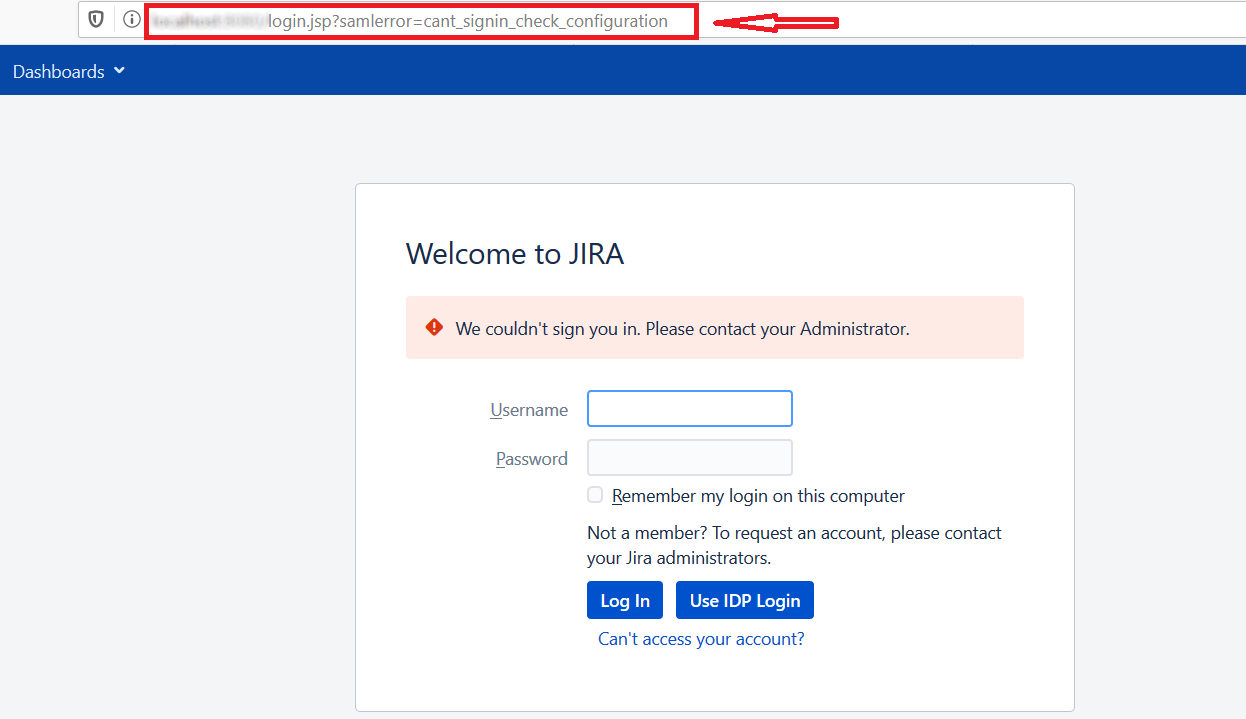
Error Code: samlerror=cant_signin_check_configuration
Description: This issue is caused by multiple reasons and all are listed below.
The creation of new users may be restricted.
How can it be fixed?
Please uncheck the new user creation in the User's Group tab of the plugin.
2. It seems multiple users exits with the same email address.
How can it be fixed?:
Please ensure email for all users should be unique if you have enabled Login with email in the Users profile tab of the plugin.
3. Username not received in the SAML Response.
How can it be fixed?:
Navigate to Configure IDP tab in plugin.
Click on the Test Configuration button.
Copy attribute name to Username.
Now, Navigate to the User's profile tab in the plugin.
Paste copied attribute name Username text field.
Save Settings.
If you are looking for anything which you cannot find, please drop us an email on info@xecurifty.com